Currently, there are many websites that have been attacked by hackers, hackers can change all files on the system by exploiting vulnerabilities that exist on websites and uploading backdoors and webshells to gain control. these websites altogether. Today I would like to present some issues related to webshell, get root and local attack.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
WebShell terminology: WebShell is a form of malicious code, a backdoor with many functions to support hackers to take control of website systems. WebShell is usually written in many languages and is often the language that the website is using. The basic function is to upload files to the server, connect to the database, bypass the security mechanisms, configure, bruteforce attack, Get Root, Local Attack… as long as the hacker can download the files. If you put this webshell on the website’s system, it is considered that the hacker has full control over that website, even if you don’t know what the account and password of this server is.
WebShell has many different types and variations, not just one file, but they are also modified by hackers into many types to easily upload engraved files to the victim’s server.

A server can have 1 or more websites developed on it, then each such website will be granted a user containing all rights to that website. An example is /user/username1. Similarly, there is also a directory /user/username2,/user/username3/, /user/username4…
Assuming /user/username2 is occupied by a hacker, with normal scripts, the hacker can access your files at /user/username1. Attacks based on scripts in one user that attack another user’s host on the same server are called local attacks.
Get Root: Also hijacking a website like Local attack but it is more sophisticated, not taking over each user like Local, but Get Root will take root of the server (root is the highest right in a Unix/Linux server). When the hacker has root privileges of the device, it means that the hacker can manage all websites on this server.
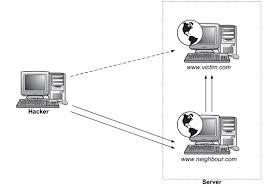
How to prevent Local Attack
The following measures will help you prevent hackers from using the local attack method
- Do not use unknown source code that is shared on the internet uncensored.
- Regularly update information about patches and vulnerabilities in the source code platform, services, and operating systems that you are using to update vendor patches.
- CHMOD logical files and folders.
- Disable functions that interact directly with the terminal (can execute shells directly into the operating system kernel) such as: exec, system, popen….
- Limit the use of shared hosting with unknown host.
- Encrypt SQL database tables containing passwords and users, set passwords containing special characters, including numbers, letters and special characters to avoid Bruteforce.
- Use virus scanners to scan the entire source code before using it and you should do this periodically to prevent hackers from inserting backdoors and malicious scripts on the server.
We hope this analysis can help you better secure your systems.