For those who Pentest or Hacker they often use Kali Linux as a tool to attack. Kali Linux seems to dominate the user market for its rich and constantly updated tools. However, not everyone is familiar with Linux, with installation and use quite complicated. Commando VM will replace Kali Linux for that on Windows platform. This is a pre-built virtual machine operating system that runs on Windows 10. Commando VM is the first Windows penetration test release released by FireEye.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
What is Commando VM?
Commando VM is a set of commands on PowerShell to install vulnerability exploit tools. You can use Commando VM right on real Windows or virtual machine VMWare, Virtual Box and turn your computer into a powerful hacking tool. The Commando VM uses the Boxstarter , Chocolatey , and MyGet packages to install all the software and tools to support penetration testing. You need at least 60GB of free hard drive space and 2GB of RAM to use it. Supports 140 tools for Hackers such as:
Hackers who want to collect Hack tools must manually install each software. Not to mention being blocked by Windows due to software that deeply interferes with the operating system. This is a difficult problem when using Windows as an attack platform.
With Commando VM allows download of Red Team tools and will remove the “malicious” features on Windows. This installer will disable many security features of Windows, implementing it will expose Windows to many vulnerabilities for this reason AnonyViet recommends you to install it on a virtual machine.
In other words: Commando VM is a code that helps to quickly install Hack tools for Hackers on Windows
Features of Commando VM
Born to be a system security testing tool. FireEye recommends that people use Commando VM for the purpose of checking the system’s safety, not using it to attack or gain unauthorized access to other systems.
“We’re looking forward to addressing user feedback, adding more tools and features, and making more improvements,” FireEye said. “We believe this distribution will become the standard tool for penetration testers and look forward to continuing to improve and develop the attack platform on Windows.”
Commando VM can be installed on Windows 7 Service Pack 1 or Windows 10. Later versions will add more features. The three outstanding features supported are:
- Native Windows protocol support (SMB, PowerShell, RSAT, Sysinternals, etc.)
- Attack Kit (Tools for Crawling, Exploiting, Password Attacks, etc.)
- Windows-based C2 frameworks like Covenant (dotnet) and PoshC2 (PowerShell)
How to install Commando VM to become an attack tool on Windows
Installing the Commando VM is pretty easy. Just Download Commando VMextract it and then execute the PowerShell script available in the package on Windows on the virtual machine to install.
Note: choose the correct version of Windows 7 or Windows 10
The rest of the installation will be done automatically, it may take 2 to 3 hours to complete depending on your Internet speed.
“VM will restart many times due to many software installation requests”. “When the installation is complete, press any key to exit PowerShell”
After the installation is complete, all you need to do is reboot the machine to make sure the final configuration changes take effect.
Prepare the virtual machine
As mentioned above, to avoid affecting the operation of Windows, you should use a virtual machine to install Commando VM. The most common are VMWare, Virtual Box, or Hyper-V…. Perform steps to create virtual machine on VMWare. Make sure your virtual machine is updated Windows to the latest version.
Start installing Commando VM and required packages
Now you have a Windows virtual machine on a real Windows.
Step 1: Download Commando VM correct version of Windows on the computer. Extract the folder to the Desktop, there will be a folder “commando-vm-master”
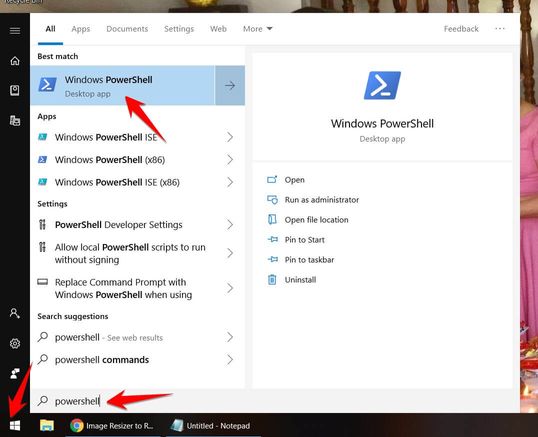
Step 2: Let’s open the tool PowerShell available on Windows up. Should open with permission Administrator
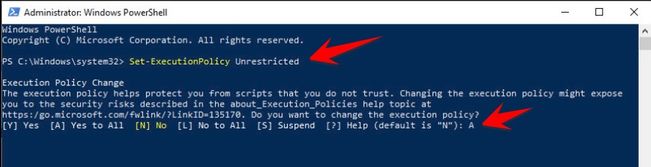
Enter the command line Set-ExecutionPolicy Unrestricted to grant execution permission.
When prompted to confirm, press A and Enter to agree to grant permission.
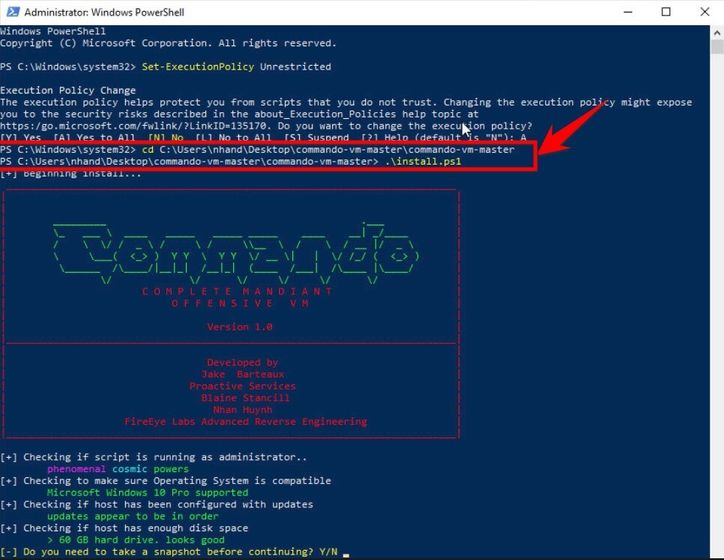
Use command cd to move back to the “commando-vm-master” folder just unzipped above. Make sure there is a file in the folder install.ps1
Type command .\install.ps1 to start the installation.
The installation process will set up the Boxstarter environment and proceed to download and install the Commando VM environment. You will be prompted to enter a Password to automatically reboot the machine during installation. If you do not set a Password, just press Enter to skip this step.
Manually install other tool packages:
Commando VM uses Chocolatey Windows manager. You can easily to install a new package. For example, enter the following command as Administrator to install Github Desktop on your system: cinst github
Update new versions for installed packages
Enter the following command to update all packages to the latest version: cup all
All tools installed:
Tools for Active Directory
- Remote Server Administration Tools (RSAT)
- SQL Server Command Line Utilities
- Sysinternals
- Covenant
- PoshC2
- WMIplant
- WMIOps
- Dep
- Git
- Go
- Java
- Python 2
- Python 3 (default)
- Visual Studio 2017 Build Tools (Windows 10)
- Visual Studio Code
- CheckPlease
- Demiguise
- DotNetToJScript
- Invoke-CradleCrafter
- Invoke-DOSfuscation
- Invoke-Obfuscation
- Invoke-Phant0m
- Not PowerShell (nps)
- PS>Attack
- PSAmsi
- Pafishmacro
- PowerLessShell
- PowerShdll
- StarFighters
- ADAPE-Script
- API Monitor
- CrackMapExec
- CrackMapExecWin
- DAMP
- Exchange-AD-Privesc
- FuzzySec’s PowerShell-Suite
- FuzzySec’s Sharp-Suite
- Generate-Macro
- GhostPack
- Rubeus
- SafetyKatz
- Seatbelt
- SharpDPAPI
- SharpDump
- SharpRoast
- SharpUp
- SharpWMI
- GoFetch
- Impacket
- Invoke-ACLPwn
- Invoke-DCOM
- Invoke-PSImage
- Invoke-PowerThIEf
- Kali Binaries for Windows
- LuckyStrike
- MetaTwin
- Metasploit
- Mr. Unikod3r’s RedTeamPowershellScripts
- NetshHelperBeacon
- Nishang
- Orca
- PSReflect
- PowerLurk
- PowerPriv
- PowerSploit
- PowerUpSQL
- PrivateExchange
- ruler
- SharpExchangePriv
- SpoolSample
- UACME
- impacket-examples-windows
- vsdown
- ADACLScanner
- ADExplorer
- ADOffline
- ADRecon
- BloodHound
- Get-ReconInfo
- GoWitness
- Nmap
- PowerView
- SharpHound
- SharpView
- SpoolerScanner
- Citrix Receiver
- OpenVPN
- Proxycap
- PuTTY
- Telnet
- VMWare Horizon Client
- VMWare vSphere Client
- VNC-Viewer
- WinSCP
- Windump
- Wireshark
- ASRERoast
- CredNinja
- DSInternals
- Get-LAPSPasswords
- Hashcat
- Internal-Monologue
- Inveigh
- Invoke-TheHash
- KeeFarce
- KeeThief
- LAPSToolkit
- MailSniper
- Mimikatz
- Mimikittenz
- RiskySPN
- SessionGopher
- DNSpy
- Flare-Floss
- ILSpy
- PEview
- Windbg
- x64dbg
- 7zip
- Adobe Reader
- AutoIT
- Cmder
- CyberChef
- Gimp
- Greenshot
- Hashcheck
- Hexchat
- HxD
- Keepass
- MobaXterm
- Mozilla Thunderbird
- Neo4j Community Edition
- Pidgin
- Process Hacker 2
- SQLite DB Browser
- Screentogif
- Shellcode Launcher
- Sublime Text 3
- TortoiseSVN
- VLC Media Player
- Winrar
- yEd Graph Tool
- Egress-Assess
- Grouper2
- zBang
- Burp Suite
- Fiddler
- Firefox
- OWASP Zap
- FuzzDB
- PayloadsAllTheThings
- SecLists