Here’s everything you need to know about the so-called “ping of death” or “ping flood” DDoS attack.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
There are a lot of scary-sounding terms in the cybersecurity world, and “ping of death” is just as dangerous. However, the way to perform the Ping of Death attack is not simple, although it is still a difficult problem to deal with as a security hole.
Let’s explore what the Ping of Death is and how it works.
“What is a ping?”
Before discovering what a “ping of death” is, we must see what a “ping” is to see how it can work against you.
A ping by itself is not dangerous. In fact, the computer does a lot of ping when you use the Internet.
Ping allows you to check if the connection has reached each other. It’s like how you say “hello”, and the other end says “hello” back.
You can even try the ping command by opening CMD and typing ping 8.8.8.8 . It’s not very interesting, since all it tells you is how many milliseconds it takes your PC to send a data packet to the target. However, it can diagnose server problems and identify vulnerabilities in failed connections.
What is a “Ping of Death” attack?
Ping is harmless in the world of computer networking. So, how could someone turn this harmless tool into a weapon?
Ping of Death is one of many types of distributed denial of service (DDoS) attacks. Usually, when people use the term “DDoS”, it refers to a series of connections that bring down the network of a certain host. However, there are many ways that a hacker can initiate a DDoS attack and Ping of Death allows an attack to be carried out with a single computer.
To do this, the hacker needs to find an old system that is connected to the internet. Because of the old system, it was established before the widespread deployment of IPv4. This is because these older networks don’t have a proper way to handle if someone sends data larger than the maximum packet of 65,535 bytes.
When hackers find this system, they will send a packet larger than the maximum size. A modern network system will detect and properly handle this huge data packet, but an older system will struggle with larger packet sizes. As a result, this can cause instability and loss of network connectivity.
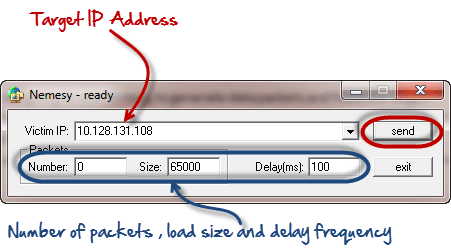
We will open CMD command to ping the victim computer with an infinite data packet of 65500
Enter the following command: ping 10.10.20.10 –t | 65500
Parameters:
- “Ping” sends data packets to the victim
- “10.10.20.10” is the IP address of the victim
- “-t” means data packets will be sent until the program stops
- “-L” specifies the data load to be sent to the victim
You will get the result as shown below: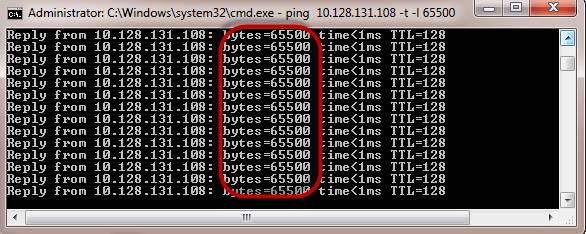
Flooding the target computer with data packets does not affect the victim much. To make the attack more effective, you should attack the target computer by pinging from multiple computers.
The above attack can be used to attack Router or Web server.
You can use Tool Nemesy to make Ping of Death easier.
How do you protect yourself from a Ping of Death?
If the above attack sounds worrisome, don’t panic. If you own the network infrastructure and new operating system versions, there is no need to worry. All you need to do is make sure your computers and network equipment are designed and upgraded after 1998, as devices manufactured after this date are designed to resist the Ping of Death.
Hopefully the PC you’re using at home isn’t too old; In fact, it can be hard for you to imagine why anyone would still use such an archaic system. Believe it or not, there are older devices and operating systems that continue to function without an upgrade. Perhaps the owner was worried that an upgrade might destabilize everything they had set up.
However, keeping a system infrequently upgraded means it becomes obsolete and vulnerable to security vulnerabilities. For example, see devastating ransomware attacks, some companies are still using Windows XP while the world is already using Windows 10.
Companies need to choose between upgrading their systems and risking incompatible software or keeping the current setup and being hacked. If they choose the latter for a very long time, it could expose them to an attack like the Ping of Death.
Ping of Death: this era is no longer dangerous
A Ping of Death attack is as easy to execute as it is destructive. As long as your hardware is from the 21st century, you have nothing to worry about.
Did you know that you can also ping devices with your Android phone? You can also do an online ping from the website to your home router at the website: https://ping.eu/ping/.