I was assigned the task of finding vulnerabilities in the Website. Before you need to do network scouting/network scouting, the term is called Recon. If used manually, it is quite time consuming, today I will introduce you to Tool reconFTW to help you scout your friends very well, integrated with many functions to help collect accurate information about the Website you are scanning.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
What is a website security vulnerability?
Website security vulnerabilities are weaknesses in the design and configuration of the system, web developer error or negligence in the operation of the website. The existence of these vulnerabilities is a danger to developers as well as website visitors when black hat hackers can fully exploit them to be able to steal your data or information. your personal information, the user’s and more

Hackers use scanning tools to detect a wide range of websites with poor security configuration or websites on popular platforms like WordPress that have published vulnerabilities that have not been addressed by the website owner or web developer, and They will use them to attack, install malicious code and destroy websites.
Some studies show that in 2019, every 45 minutes, a website will be “visited” by hackers and mainly black hat hackers. This is enough to talk about how dangerous the existence of security holes is.
Common types of website security vulnerabilities

- SQL Injection (you can see more articles use SQLmap For more details)
- Broken Authentication
- Cross Site Scripting
- Server-Side Template Injection
- Insecure Direct Object References
reconFTW is a software from the github community and authored by six2dez. This is a network reconnaissance tool, also known as a network spy, and it can collect information of the website such as the owner, the domain name is associated with but most importantly, this tool is capable of automating the process. Check your website’s security, list all subdomains, and do a comprehensive vulnerability check. reconFTW uses a variety of methods to test including:
- passive
- bruteforce
- permutations
- certificate transparency
- source code scraping
- analytics
- DNS records
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL check, SSTI,DNS, etc. Along with that, reconFTW can OSINT (trace tracing) and scan target’s port.
To say, compared to tools like Burpsuite, in terms of features, they are not inferior to them but also can run the tool simply and easily. After experiencing, this is an extremely suitable tool for those of you who cannot use tools like nmap or Burpsuite.
At the same time, after the whole detective process has been completed, all that has been collected will be aggregated into a single file and it is quite convenient if you want to reopen it to check and check for possible errors. available on the website.
It takes a long time to run the entire network reconnaissance feature, but I just need to sit and eat because the whole process has been automated and optimized so that the user can easily. collect information
Note before doing
It is strictly forbidden to take advantage of the security holes of non-proprietary websites to wreak havoc. Anonyviet will not be responsible for any of your actions. Please continue if you already agree with this note!
Instructions for using reconFTW to scan website security holes
Installation Instructions
You can visit the official tool’s github link here
For live installation / using virtual machine / using VPS
git clone https://github.com/six2dez/reconftw cd reconftw/ ./install.sh #khởi động tool ./reconftw.sh -d [tên miền] -r
For Docker
Method 1: From DockerHub
docker pull six2dez/reconftw:main wget https://raw.githubusercontent.com/six2dez/reconftw/main/reconftw.cfg mkdir Recon #câu lệnh khời động tool docker run -d -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm six2dez/reconftw:main -d [tên miền] -r
Method 2: from Github
git clone https://github.com/six2dez/reconftw cd reconftw docker build -t reconftw Docker/. #câu lệnh khởi động tool docker run -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm reconftw -d [tên miền] -r
User manual
Syntax: ./reconftw.sh [tùy chọn dành cho mục tiêu] [Input cho mục tiêu] [chế độ(mode)] [các tùy chọn khác]
For option for target
Here:
Target.com is the domain you want to attack
-r: I will explain in the mode (mode)
- -d: for 1 domain name
For example:./reconftw.sh -d target.com -r - -l: use a list of domains
For example:./reconftw.sh -l targets.txt -r - -m: for 1 target but multiple domains
For example:./reconftw.sh -m target -l domains.txt -r - -i: add subdomains as list
For example:./reconftw.sh -d target.com -i in.txt -r - -x: exclude subdomains
For example:./reconftw.sh -d target.com -x oos.txt -r
For modes
Usually, I recommend using -r over the others because I only use that. If you want full scan, use -a
Note: processing speed depends on the mode you choose and the speed of your home network. Sometimes with large web it will take quite a while.
- -r: Website scouting with all modes (no attack)
For example:./reconftw.sh -d target.com -r - -S: Search Subdomains
For example:./reconftw.sh -d target.com -s - -p: Only run as passive
For example:./reconftw.sh -d target.com -p - -w: Check the website provided in the list
For example:./reconftw.sh -l targetlist.txt -w - -a: Run all functions
For example:./reconftw.sh -d target.com -a - -n: osint – tracing
For example:./reconftw.sh -d target.com -n - -H: show help
For example:./reconftw.sh -h
For other options
- –deep: Run deep scan
- -v: VPS – use when you run on VPS
- -f conf_file: use another config (not recommended)
- -o: Save output of reconFTW
Some examples of usage
- Run web snooping with a unique domain name:
./reconftw.sh -d target.com -r - Run web scouting with a list of domains:
./reconftw.sh -l sites.txt -r -o /output/directory/ - Run web scouting with a list of domains on vps:
./reconftw.sh -d target.com -r --deep -o /output/directory/ - Run web snooping with multiple domains from 1 company:
./reconftw.sh -m company -l domains_list.txt -r - Boot into Full power mode:
./reconftw.sh -d target.com -a
Eg:

Actual Demo
First, I run the following command: ./reconftw.sh -d duocphamviethung.com.vn -r
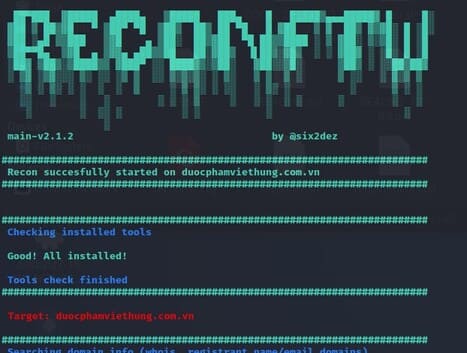
After it finishes scanning, it returns the results. There is a statistics of the time it takes to scan and complete the task. Currently, it has taken me up to 2 hours for a small website, so please note the time!
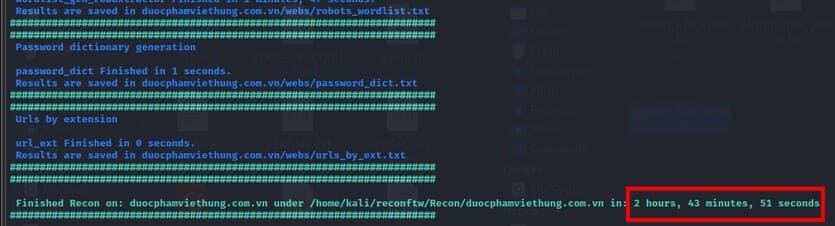
All files are saved in folder Recon/[tên website tấn công] if you don’t set its output. 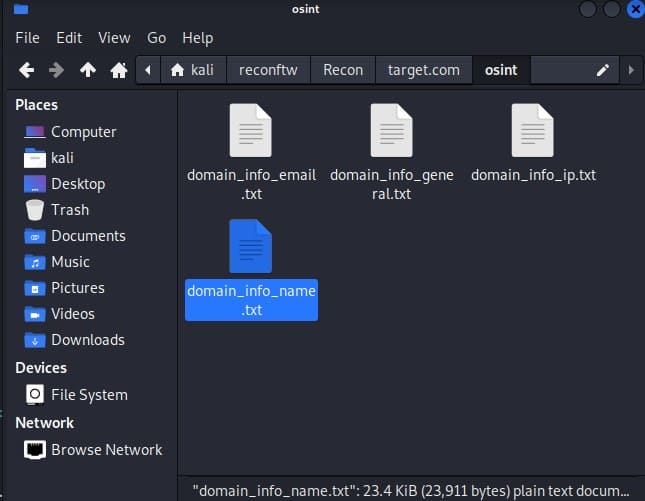
Here, the file that you need to pay attention to is the nuclei_output file because this file will return a CVE error code that hackers can use to exploit information. You can go to Google and search for the error code to find the solution to fix it as soon as possible!
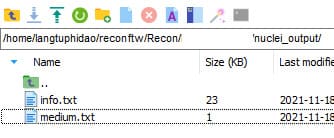
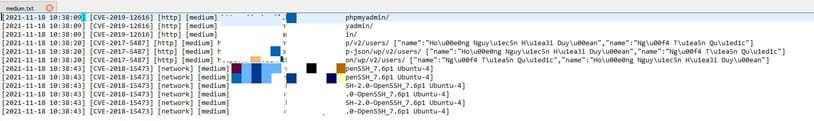
Use it to pentest your system only!