Google Dorking is pushing Google Search to its limits, using advanced search operators to tell Google exactly what you want. Many people consider it a Data Stealing Technique to find unprotected sensitive information about a company, but I consider it a Hacker’s Way of Thinking because I use Google Dorks for more purposes than security research. secret.
| Join the channel Telegram of the AnonyViet 👉 Link 👈 |

The first time I realized the power of Google Dork was when I searched for the Cisco Anyconnect software used to connect to Cisco VPNs. However, Cisco does not allow software downloads, and a search for “Cisco Anyconnect” leads to many websites that only talk about software. I’ve been looking at Google’s advanced search operators and found that I can search the titles of web pages. After seeing that I could search by HTTP Headers, I came up with the idea that if I search for “Open Directory Listings”, the results will only be files. I changed my search query to intitle: index.of cisco anyconnect and suddenly I found loads of results. Finally, I downloaded the executable and then generated the MD5sum hash of the file, then compared it to what’s on the Cisco website. After I found a matching file, I knew it hadn’t been tampered with and could run safely.
At the time, I didn’t know this was called Google Dorking, but until I came across BlackHat’s presentation. Google Hacking for Penetration Testersthen I realized the full power of Google.
Advanced search operator
Using Advanced Search Operators allows you to find almost anything you want on the web. Most people know about queries like site:hackthebox.com ext:pdf to display all PDF files hosted on a domain. This can often be combined with exiftool to extract metadata from documents revealing usernames, dates, and potential software used. However, many people don’t think of using it against cloud storage like site: drive.google.com hackthebox. Thankfully, this search result doesn’t come up too often. Google does not crawl drive.google.com itself, but instead searches for documents posted on the public internet. My favorite Google Dorks are:
Try to apply by Hack email with Google Dork let see.
Website and INURL
Operators check the URL, I use the site most often because many sites have bad self-search functionality. For example, if you used Reddit’s built-in search to search for ippsec and then used Google Search: site: reddit.com ippsec, you would probably get completely different results.
The INURL part is valid if you’re looking for a term in the URL but don’t care on which web page it’s used. This is often used to measure the impact that web mining can have. For example, if a vulnerability appeared with a WordPress plugin, I would look for the plugin’s filename and use inurl: file_used_by_plugin.php and see how many sites could be affected by this vulnerability. Then I would create a list of bug bounty sites or participate in programs like Synack and then check if any of them appear on the list.
To exclude, to expel –
Whenever a Google query is executed, placing a dash will subtract that query from the results. This is extremely useful when trying to remove web pages or parts of URLs from the results. Using -site: website.com will ensure that the site doesn’t appear in your search results. This is also useful with inurl: piece because it can remove parts of the web page from the results.
Before and after
Google keeps records of when pages were first seen or last modified. Using the before/after tag is a great way to narrow down your search. There have been many times when a recent headline fills up Google search results. Adding the before: tag is a great way to get rid of that. Also, when an error occurs, I usually use the after:
Caching
Websites will often show different information to search engines for Search Engine Optimization (SEO) reasons. Using cache:url will allow you to view a web page returned to Google. This is useful when the site is hiding information after a single login. There is a misunderstanding around this feature, I have seen many people refer to this as “Passive Recon” which means that if you view a website through google cache it will not know you visited. access it. This is not true because normally Google’s cache will not record some autoload links when viewing cached results and your browser will still make requests to the item web server pepper.
Google Advanced Search
If you navigate to google.com/advanced_search, you’ll see a page that helps create a Google Dork and shows the syntax for performing a search. The most interesting setting is being able to change the area to display the results. Google provides the results it thinks are of interest to you, and one of the main determining factors is where you are. For example, if I do a Search “Google”, the first result will go to google.com. If I change the regional setting to UK it gives me the google.co.uk website. This can be useful for sorting out the different countries an organization has its infrastructure in. However, not all Google Dorks are for OSINT, which is equally useful for finding foreign news. Since I’m in Vietnam, if I search for UK-related news, Google will still prioritize Vietnamese websites that cover UK news. If I do the same search related to UK but change the regional setting to UK, it will now favor UK local sites over Vietnam.
Examples of LinkedIn
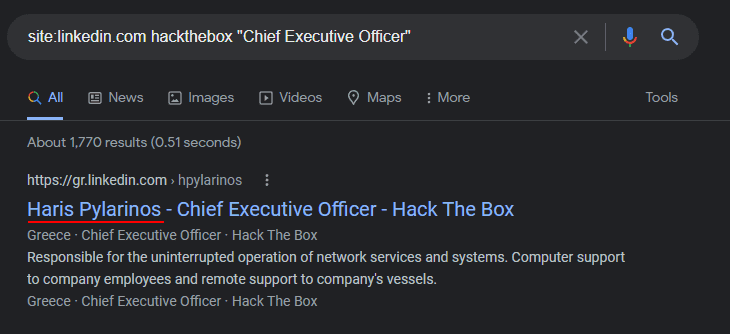
My favorite demo of Google Dorking is with LinkedIn because I use it in most of my interactions to improve the amount of information gathered during the OSINT phase. When you use LinkedIn to view employees of a company and do not have any connection to a person, LinkedIn will only show you their avatar, title, and location. You don’t have a link to go to that person’s actual profile.
However, if you search like: linkedin.com jobtitle, Google will usually find a LinkedIn profile for you, which reveals their name. Also, remember LinkedIn is a global company. If the company I’m looking for employees in is in a different country than me, I’ll usually change my regional settings to match that company.
Learn more about Google Dorks
There’s so much more about Google Dorking beyond what I’ve talked about here, by far the best resource to visit is Exploit-DB’s Google Hacking Database. I am sure that when you start reading Google Dorks, you will find a lot of useful ideas for you. Otherwise, search for different cloud service providers like Google Drive, OneDrive, Dropbox, etc. and see how you can use Google to crawl those documents.
The google Pentest-Tools hack page is a great way to get started with Google Dorking. I really like this site because it offers 14 different types of Google Dorks, such as searching for documents, logs or configuration files, and then opening Google Search on a new page. This is a great way to get started with Google Dorking as it guides you through some of the popular Google Dorks. However, in the end, you should be less dependent on this tool as it can limit creativity.
Using automated tools
There are many automated tools that will run a large number of Google dorks for you and output text files for you to peruse. This is beneficial because the main time consuming part of Google Dork is clicking through all of the Google pages. If you just want a list of all the PDFs on a web page, it will take longer to write each URL than 10 URLs at a time (default results per page). These tools change quite often so it’s hard to say which is the best, usable site:github.com after:(6 months ago) Google Dork and look for the most up-to-date tools. However, one of the tools I like to use the most is dork scanner.
Google Hacking Dork 2022
Get Email Address from Google Dork?
site:facebook.com "anonyviet" "@gmail.com" Hoặc nếu bạn muốn ID email theo địa danh thì hãy sử dụng Dork sau site:facebook.com "anonyviet" "singapore" "@gmail.com"
Find security holes with Google Dork
intext:bounty inurl:/security inurl:"bug bounty" and intext:"€" and inurl:/security inurl:"bug bounty" and intext:"$" and inurl:/security inurl:"bug bounty" and intext:"INR" and inurl:/security
Google queries to locate Web Servers
"Apache/1.3.28 Server at" intitle:index.of Apache 1.3.2 "Apache/2.0 Server at" intitle:index.of Apache 2.0 "Apache/* Server at" intitle:index.of any version of Apache "Microsoft-IIS/4.0 Server at" intitle:index.of Microsoft Internet Information Services 4.0 "Microsoft-IIS/5.0 Server at" intitle:index.ofMicrosoft Internet Information Services 5.0 "Microsoft-IIS/6.0 Server at" intitle:index.of Microsoft Internet Information Services 6.0 "Microsoft-IIS/* Server at" intitle:index.of any version of Microsoft Internet Information Services "Oracle HTTP Server/* Server at" intitle:index.of any version of Oracle HTTP Server "IBM _ HTTP _ Server/* * Server at" intitle:index.of any version of IBM HTTP Server "Netscape/* Server at" intitle:index.of any version of Netscape Server "Red Hat Secure/*" intitle:index.of any version of the Red Hat Secure server "HP Apache-based Web Server/*" intitle:index.of any version of the HP server Queries for discovering standard post-installation intitle:"Test Page for Apache Installation" "You are free" Apache 1.2.6 intitle:"Test Page for Apache Installation" "It worked!" "this Web site!" Apache 1.3.0 – 1.3.9 intitle:"Test Page for Apache Installation" "Seeing this instead" Apache 1.3.11 – 1.3.33, 2.0 intitle:"Test Page for the SSL/TLS-aware Apache Installation" "Hey, it worked!" Apache SSL/TLS intitle:"Test Page for the Apache Web Server on Red Hat Linux" Apache on Red Hat intitle:"Test Page for the Apache Http Server on Fedora Core" Apache on Fedora intitle:"Welcome to Your New Home Page!" Debian Apache on Debian intitle:"Welcome to IIS 4.0!" IIS 4.0 intitle:"Welcome to Windows 2000 Internet Services" IIS 5.0 intitle:"Welcome to Windows XP Server Internet Services" IIS 6.0 Querying for application-generated system reports "Generated by phpSystem"
Find OS version, hardware configuration, logged in users, open connections, RAM and free disk space…
"This summary was generated by wwwstat" web server statistics, system file structure "These statistics were produced by getstats" web server statistics, system file structure "This report was generated by WebLog" web server statistics, system file structure intext:"Tobias Oetiker" "traffic analysis" systemperformance statistics as MRTG charts, network configuration intitle:"Apache::Status" (inurl:server-status | inurl:status.html | inurl:apache.html) server version, operating system type, child process list, current connections intitle:"ASP Stats Generator *.*" "ASP Stats Generator" "2003-2004 weppos" web server activity, lots of visitor information intitle:"Multimon UPS status page" UPS device performance statistics intitle:"statistics of" "advanced web statistics" web server statistics, visitor information intitle:"System Statistics" +"System and Network Information Center"
System performance statistics in the form of MRTG charts, hardware configurations, running services
intitle:"Usage Statistics for" "Generated by Webalizer" web server statistics, visitor information, system file structure intitle:"Web Server Statistics for ****" web server statistics, visitor information nurl:"/axs/ax-admin.pl" -script web server statistics, visitor information inurl:"/cricket/grapher.cgi" MRTG charts of network interface performance inurl:server-info "Apache Server Information" web server version and configuration, operating system type, system file structure "Output produced by SysWatch *" operating system type and version, logged users, free memory and disk space, mount points, running processes, system logs
Find the Admin login link of the Website
admin1.php admin1.html admin2.php admin2.html yonetim.php yonetim.html yonetici.php yonetici.html admin/account.php admin/account.html admin/index.php admin/index.html admin/login.php admin/login.html admin/home.php admin/controlpanel.html admin/controlpanel.php admin.php admin.html admin/cp.php admin/cp.html cp.php cp.html administrator/ administrator/index.html administrator/index.php administrator/login.html administrator/login.php administrator/account.html administrator/account.php administrator.php administrator.html login.html modelsearch/login.php moderator.php moderator.html moderator/login.php moderator/login.html moderator/admin.php moderator/admin.html account.php account.html controlpanel/ controlpanel.php controlpanel.html admincontrol.php admincontrol.html adminpanel.php adminpanel.html admin1.asp admin2.asp yonetim.asp yonetici.asp admin/account.asp admin/index.asp admin/login.asp admin/home.asp admin/controlpanel.asp admin.asp admin/cp.asp cp.asp administrator/index.asp administrator/login.asp administrator/account.asp administrator.asp login.asp modelsearch/login.asp moderator.asp moderator/login.asp moderator/admin.asp account.asp controlpanel.asp admincontrol.asp adminpanel.asp fileadmin/ fileadmin.php fileadmin.asp fileadmin.html administration/ administration.php administration.html sysadmin.php sysadmin.html phpmyadmin/ myadmin/ sysadmin.asp sysadmin/ ur-admin.asp ur-admin.php ur-admin.html ur-admin/ Server.php Server.html Server.asp Server/ wp-admin/ administr8.php administr8.html administr8/ administr8.asp webadmin/ webadmin.php webadmin.asp webadmin.html administratie/ admins/ admins.php admins.asp admins.html administrivia/ Database_Administration/ WebAdmin/ useradmin/ sysadmins/ admin1/ system-administration/ administrators/ pgadmin/ directadmin/ staradmin/ ServerAdministrator/ SysAdmin/ administer/ LiveUser_Admin/ sys-admin/ typo3/ panel/ cpanel/ cPanel/ cpanel_file/ platz_login/ rcLogin/ blogindex/ formslogin/ autologin/ support_login/ meta_login/ manuallogin/ simpleLogin/ loginflat/ utility_login/ showlogin/ memlogin/ members/ login-redirect/ sub-login/ wp-login/ login1/ dir-login/ login_db/ xlogin/ smblogin/ customer_login/ UserLogin/ login-us/ acct_login/ admin_area/ bigadmin/ project-admins/ phppgadmin/ pureadmin/ sql-admin/ openvpnadmin/ wizmysqladmin/ vadmind/ ezsqliteadmin/ hpwebjetadmin/ newsadmin/ adminpro/ Lotus_Domino_Admin/ bbadmin/ vmailadmin/ ccp14admin/ irc-macadmin/ banneradmin/ sshadmin/ phpldapadmin/ macadmin/ administratoraccounts/ admin4_account/ admin4_colon/ radmind-1/ Super-Admin/ AdminTools/ cmsadmin/ phpSQLiteAdmin/ server_admin_small/ database_administration/ system_administration/
SQL injection Dork 2022
Update Imp. Dorks. Dork : "inurl:dettaglio.php?id=" Exploit : www.victim.com/sito/dettaglio.php?id=[SQL] Example : http://www.cicloposse.com/dettaglio.php?id=61' Dork: inurl:prodotto.php?id) Exploit: www.victim.com/prodotto.php?id=[SQL] Example: http://www.poderimorini.com/en/prodotto.php?id=14' allinurl: \"index php go buy\" allinurl: \"index.php?go=sell\" allinurl: \"index php go linkdir\" allinurl: \"index.php?go=resource_center\" allinurl: \"resource_center.html\" allinurl: \"index.php?go=properties\" allinurl: \"index.php?go=register\"
Database error messages, potentially containing function names, filenames, file structure information, SQL snippets, and passwords
"A syntax error has occurred" filetype:ihtml
Authorization error, potentially containing usernames, function names, file structure information, and SQL snippets
"Access denied for user" "Using password"
PHP errors related to permissions, potentially containing filenames, function names, and file structure information
"The script whose uid is" "is not allowed to access"
Oracle database error, potentially containing file names, function names, and file structure information
"ORA-00921: unexpected end of SQL command"
Cocoon errors, potentially containing Cocoon version information, filenames, function names, and file structure information
"error found handling the request" cocoon filetype:xml
Invision Power Board error, potentially containing function names, filenames, file structure information, and SQL snippets
"Invision Power Board Database Error"
MySQL database error, potentially containing username, function name, filename, and file structure information
"Warning: mysql _ query()" "invalid query"
CGI script errors, potentially containing operating system and program version information, user names, filenames, and file structure information
"Error Message : Error loading required libraries."
MySQL database error, potentially containing information about database structure and content
"#mysql dump" filetype:sql
Google Dork find Website Password
The site password, stored as the string “http://username:password@www…”
http://*:*@www" site
Backup file, potentially containing username and password
filetype:bak inurl:"htaccess|passwd|shadow|ht users"
mdb file, potentially containing password information
filetype:mdb inurl:"account|users|admin|admin istrators|passwd|password"
File pwd.db, potentially containing password information
intitle:"Index of" pwd.db
Folder with Admin information related to backup
inurl:admin inurl:backup intitle:index.of
WS_FTP configuration file, possibly containing the password to access the FTP server
"Index of/" "Parent Directory" "WS _ FTP.ini"
filetype:ini WS _ FTP PWD
File containing Microsoft FrontPage password
ext:pwd inurl:(service|authors|administrators |users) "# -FrontPage-"
The file containing the SQL code and password is inserted into the database
filetype:sql ("passwd values ****" | "password values ****" | "pass values ****" )
Trillian IM . configuration file
intitle:index.of trillian.ini
Eggdrop configuration file ircbot
eggdrop filetype:user
OpenLDAP configuration file
filetype:conf slapd.conf
WV Dial config file
inurl:"wvdial.conf" intext:"password"
Eudora mail client configuration file
ext:ini eudora.ini
Microsoft Access file, potentially containing user account information
filetype:mdb inurl:users.mdb
Searching for private data and confidential documents
File email.xls, potentially containing contact information
filetype:xls inurl:"email.xls"
Find someone’s job application
"phone * * *" "address *" "e-mail" intitle: "curriculum vitae"
Confidential document containing confidentiality clause
"not for distribution"
Contacts AIM
buddylist.blt
Contacts Trillian IM
intitle:index.of mystuff.xml
MSN Contacts
filetype:ctt "msn"
QDF database file for Quicken . financial application
filetype:QDF
Find information about finance, banking, credit cards
intitle:index.of finances.xls
Find Log Mail, possibly containing Email
intitle:"Index Of" -inurl:maillog maillog size
Report of security vulnerability scanning software
"Host Vulnerability Summary Report"
filetype:pdf "Assessment Report"
"This file was generated by Nessus"
Google Dork finds networked devices
"Copyright (c) Tektronix, Inc." "printer status"
PhaserLink printers
inurl:"printer/main.html" intext:"settings"
Brother HL printers
intitle:"Dell Laser Printer" ews
Dell printers with EWS technology
intext:centreware inurl:status
Xerox Phaser 4500/6250/8200/8400 printers
inurl:hp/device/this.LCDispatcher
HP printers
intitle:liveapplet inurl:LvAppl
Canon Webview webcams
intitle:"EvoCam" inurl:"webcam.html"
Evocam webcams
inurl:"ViewerFrame?Mode="
Panasonic Network Camera webcams
(intext:"MOBOTIX M1? | intext:"MOBOTIX M10?) intext:"Open Menu" Shift-Reload
Mobotix webcams
inurl:indexFrame.shtml Axis
Axis webcams
intitle:"my webcamXP server!" inurl:":8080?
webcams accessible via WebcamXP Server
allintitle:Brains, Corp.
camera webcams accessible via mmEye
intitle:"active webcam page"